Use cases
Secure CAN Bootloading
It is quite common, that devices with CAN interface also support updating its firmware via the CAN interface. In the past, the security protection for such bootloaders was often minimal, as the CAN network was mostly a “closed” network. Starting a firmware update was only possible with physical access to the network.
Today, more and more CAN networks feature remote access to support diagnostic functions or IoT data mining or access. This gives intruders additional attack vectors and Embedded Ransomware attacks (link to blog article) can become a reality, if the bootloading process is not properly secured.
Secure CAN-FD Bootloading with NXP LPC54618
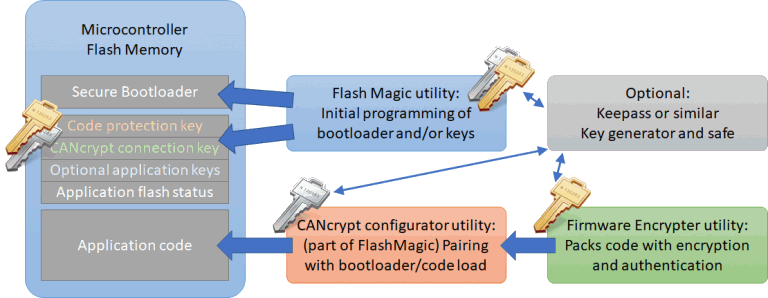
Our secure bootloader implementation uses two symmetric keys to protect both the code and the bootloader activation process separately. The manufacturer uses a code protection key to encrypt and authenticate the firmware (here using AES-GCM). An additional CANcrypt connection key is used to connect an authorized update utility to the bootloader. This allows an additional protection level, as only an authorized system integrator, technician or utility can activate the bootloader in the first place.
The initial keys, bootloader and firmware need to be programmed in a secure, trusted environment:
- On initial production of the device, the bootloader and the default code protection and CANcrypt connection keys get programmed. This must happen in a secure environment. The Flash Magic programming utility can be used.
- The original firmware can be programmed at the same time.
The firmware update process now requires the following steps:
- The manufacturer generates a new firmware update file using a firmware encrypter utility. This uses the code protection key (must match key stored in target device). NOTE: If key is unknown: each symmetric key also has a public key ID, this public key ID can be read from the bootloader and then used by manufacturer to recognize the matching key.
- The system integrator or service technician or “task” activating the bootloader must
- know the CANcrypt connection key (could be replaced by system integrator or builder at the time of first installation of the device)
- have a copy of the encrypted firmware update file
- The bootloader is activated by a CANcrypt connection based on the CANcrypt connection key
- Once the bootloader is activated, the firmware update file is transferred to the bootloader and flashed into the device
- The firmware update only completes, if firmware update file is properly authenticated using the code protection key